On a recent Monday morning, I got a panicked call from one of my clients. Someone in their accounting department had been hit with file-encrypting malware. Even worse, they had the company-wide shared drive connected at the time, so hundreds of files had been affected.
We’ll never know for certain exactly what happened to let the malware in. The problem wasn’t discovered until Monday but the time stamps on the encrypted files were all from the previous Friday. The company had been in the process of an email migration and Outlook upgrade. A few people had been working on the laptop in question, and no one remembers doing anything which would have run the malware. Based on several other stories, this is most likely how the company became infected:
You might be wondering from what server the Word macro downloads the encrypting program, and why its address isn’t blocked by anti-virus software.
It turns out that a lot of effort goes into making new servers (or at least URLs) faster than the anti-virus companies can keep up. For a deeper look into how this works, here’s an interesting article about it.
- The finance team received an email claiming to include an invoice as an attached Microsoft Word document.
- When opened, the Word document contained gibberish. But there was also a message suggesting that the unreadable mess was due to a decoding error, and enabling macros would fix it.
- As soon as macros were enabled, the malware script started, which downloaded and ran the program that did the actual encrypting.
- The Word document didn’t change, and the unfortunate victim probably just closed it and deleted the email, but the damage had already been done.
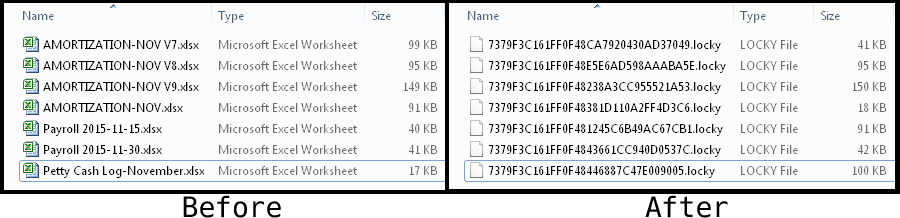
Encrypted Files
After the encryption program had finished doing its dirty work, any files it chose to attack were renamed and encrypted. Although there are claims on the web that the Locky ransomware will target a large list of file types, only Word, Excel, and PowerPoint documents were hit in our case. There’s evidence that the infected laptop was shut down before Locky could process all the files on the shared drive, so this limited set of targeted files may just be a fluke of circumstance.
Folder names were not changed, so there was enough information to know the general subject areas of the hostage files. But there was no way to know exactly what the files used to contain. There’s no practical way to decrypt the files, or even know what their original names were, without the key.
In this state, there were four possible options:
- Restore the files from backups
- Attempt to recover deleted versions of the files
- Pay for the decryption program
- Live without the files
Backups, what backups?
Everyone knows they should back up their files frequently. Most people know that you should test your backups and confirm you can restore your files if you ever need to. Many people know these things and still fail to do them, like us.
Un-deleting files
When you search the web and find blogs with titles like “Decrypt .locky files and remove Locky virus,” you’re sure to be disappointed. The blogs with these misleading titles do not tell you how to decrypt your files. Instead, these unethical individuals are another layer of predator, trying to take advantage of desperate people who just want their files back. What they really do is convince you to download multiple programs that will supposedly clean your system of the Locky virus and get your original files back by finding the deleted copies on your hard disk.
If you download and run these programs, you’ll be presented with a scary list of alleged “problems” that the software offers to fix. Click the “Fix All” button, and BAM! you’re blocked until you register, give your real name, hand over your email address, and of course pay. And those blog authors who claimed they were helping you decrypt your files? They get a cut, of course.
In theory, if you could recover deleted files, you might be OK. It depends whether you need to know you have the most recent version of every file, or can live with getting some stuff back and losing the rest.
In our case, we ran some undelete utilities and they recovered several deleted files. We had no way of knowing whether the deleted files they recovered were the most recent versions, or older versions that had been thrown in the trash along the way. Even worse, the number of files we were able to undelete was less than the number of encrypted .locky files. So we knew that we were still missing some files, but thanks to the renaming, we didn’t know which ones!
Ransom Demand
Whether to pay the ransom or live without the files wound up being a business decision. The factors that went into the decision included:
- The cost of losing the files permanently
- The cost of the ransom
- The risk that the criminals would run off with the money and not provide the decryption key
- Our willingness to encourage the criminals by giving in to their demands
In reality, the criminals are generally not stupid. They set a ransom amount that is low enough that people are willing to take the risk and don’t feel too badly about giving in. They’re also usually smart enough to live up to their end of the deal and provide the decryption key. If they got a reputation for not delivering, people would stop paying.
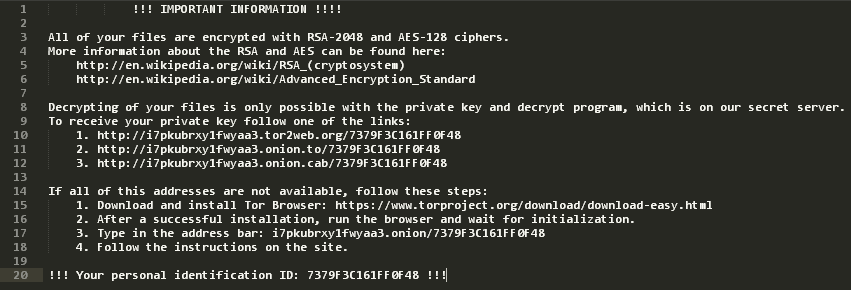 Inside every folder containing encrypted files, the malware also placed a short text file with instructions. The instructions, shown above, were just the first step. All they did was point us at a site on the dark web where the actual ransom demand could be found.
Inside every folder containing encrypted files, the malware also placed a short text file with instructions. The instructions, shown above, were just the first step. All they did was point us at a site on the dark web where the actual ransom demand could be found.
The first, and easier, set of instructions with standard web links didn’t work. Those sites are unofficial proxies between regular web browsers and the dark web sites that can only be reached as hidden services through the Tor network. In two of the three cases, the proxies identified that the links were part of a ransomware scheme and refused to access the content.
The Tor Browser was easy to install and run, so we set it up and went to the address in the instructions.
This answered the question about the amount of the ransom. At the time, the USD equivalent of 3.0 Bitcoins was about $1,233. After weighing the pros and cons, especially the cost of any work required to recreate documents or to verify undeleted documents, my client made the decision to pay the ransom.
Despite the clear instructions and helpful recommendations in the ransom demand, we found that buying Bitcoins to pay the ransom was not a fast process. The Bitcoin wallet and exchange web site we selected turned out to have their own set of shady practices. After getting to this point and deciding to pay the ransom, everything paused for about a week while we acquired Bitcoins. Read all about that process in part 2 of this story.